Database access control
Database access control is responsible for control of rules determined for all direct accesses to the system by security policies . Traditional control systems work with notions subject, object and operation.
For better understanding look at the figure of secure DBMS (DataBase Management System ).
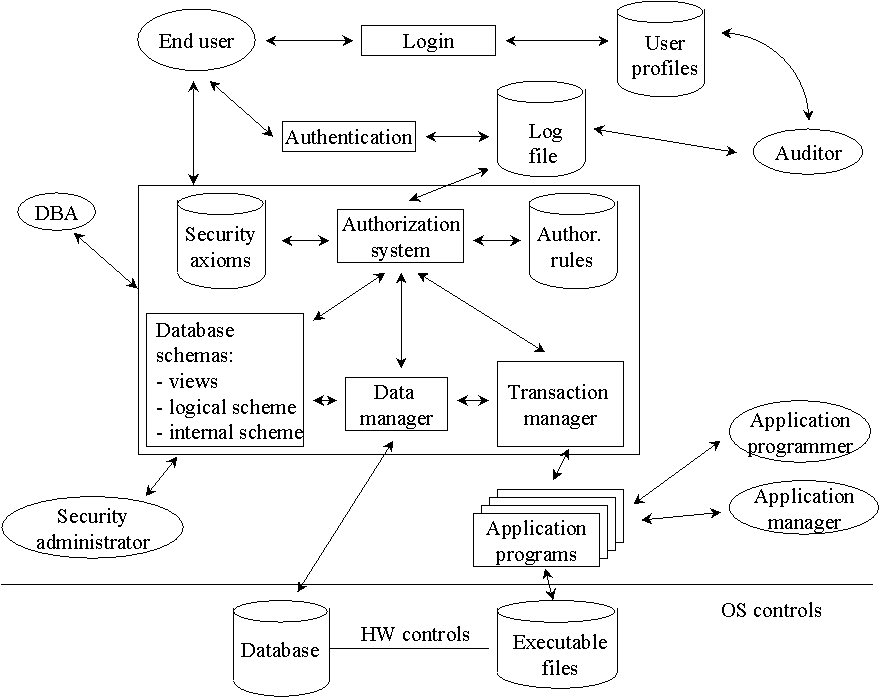
Security Models
The goal of security modeling is to create abstract, software independent, conceptual model from requirements specification for system protection.
Security model must gives rich semantic representation which allows description of functional and structural properties of security system. It should also give definitions for protection requirements and system policies. The proof of model properties should be available, too.
It is clear that level on which we decide to describe access control can greatly differ. Description of concrete models follows.
Abstractions of Access Models
Access control models can be classified in several levels as proposed by LaPadula and Williams. Following levels proceed from general to more implementation dependent:
- trust objectives – definition of basic requirements on the system trustfulness
- requirements on external interface – security requirements on interface system-environments
- internal requirements – requirements that must be satisfied in system components
- operational rules – describe assurance of internal requirements
- functional design – functional description of behavior of system components
Types of Access Control Models
Security models can be classified according to many factor. For an instance target system, type of security policy, addressed security aspects, type of control (direct or of flows) and so on. In the moment we will talk about type of security policy that is enforced by the model.
Two basic model types rised very soon – discretionary and mandatory access control. Owner of data governs access in the former one. This is the most common form of authorization administration – ownership based. That policy is very flexible but also very difficult for control from the global point of view. Models with mandatory access control enforce global policy by the flow control among security levels that are assigned to objects.
It seemed that nothing else would exist but OO technologies have encourage new approaches that reflect OO DBMSs and new requirements of commercial sphere. The first one is RBAC – access control based on roles and the second one is TBAC which is based on concept of task. TBAC brings absolutely new ideas and notion of active security.

